User:Gnyers/InteropDemo/SambaAsMemberServerInADDomain
Tested on openSUSE
Recommended articles
Integrating with Active Directory as authentication and authorization source is a frequent use case in mixed Linux and Windows environments. Winbind, a component of Samba, provides not only the necessary integration with AD but also a PAM module to authenticate and authorize Linux users
This HOWTO uses Samba 3.6
Introduction
Integrating with Active Directory as authentication and authorization source is a frequent use case in mixed Linux and Windows environments. Winbind, a component of Samba, provides not only the necessary integration with AD but also a PAM module to authenticate and authorize Linux users.
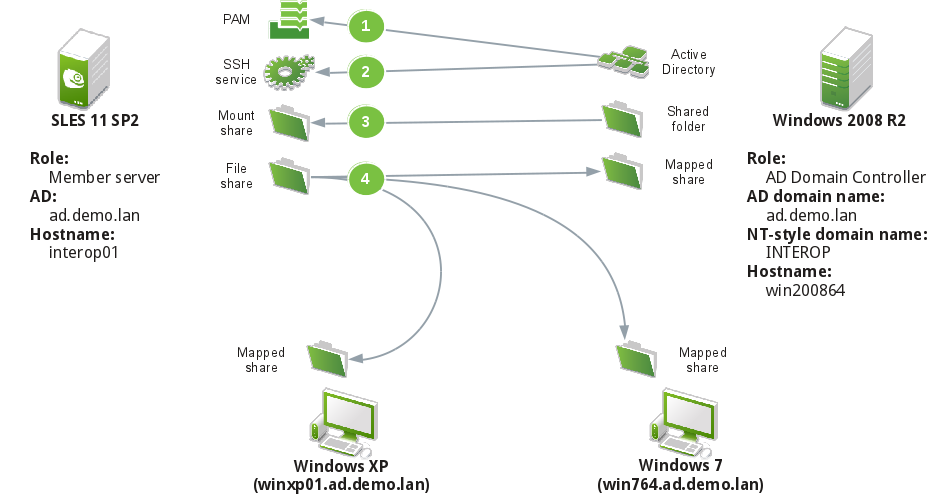
- Use cases 1 and 2: Use Active Directory for authentication and authorization
- Use case 3: Accessing Windows file shares (/etc/smb/smbfstab or /etc/fstab)
- Use case 4: Provide a share for Windows clients
Integrating with Active Directory
Configuring Winbind on SLES
Join Active Directory domain
| Step | Notes | Screenshot | |
|---|---|---|---|
| 1. |
Start YaST |
||
| 2. |
Select "Network Services" > "Windows Domain Membership |
||
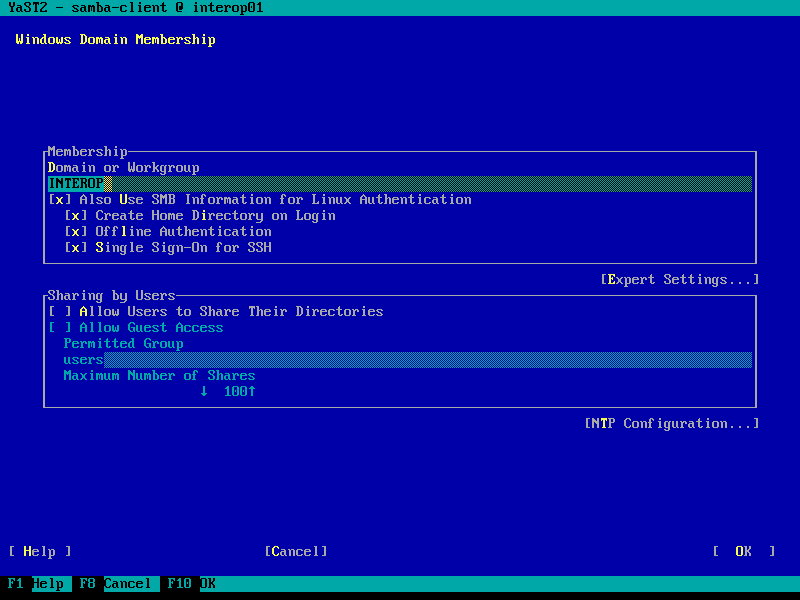
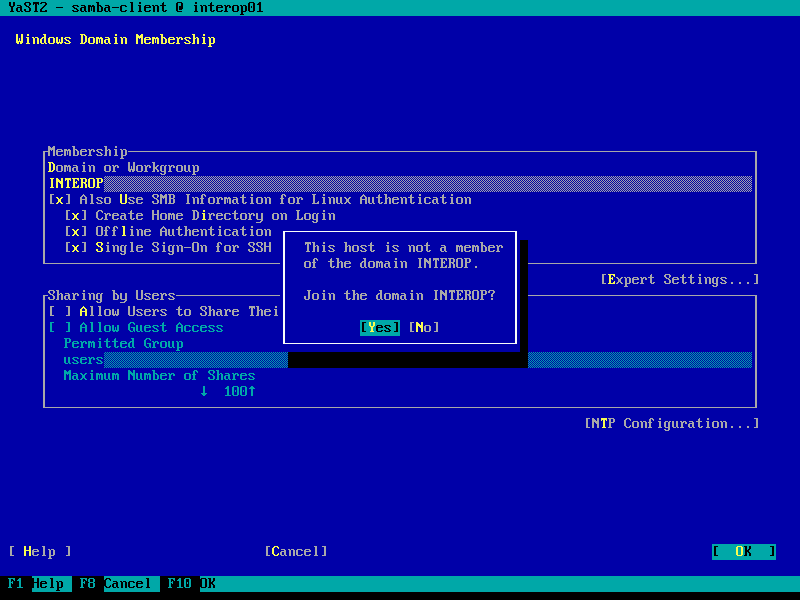
| 3. | Fill in domain details | ||
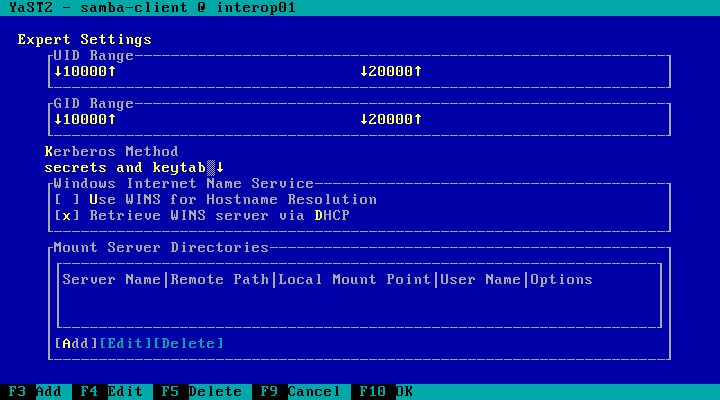
| 4. |
Expert Settings
|
||
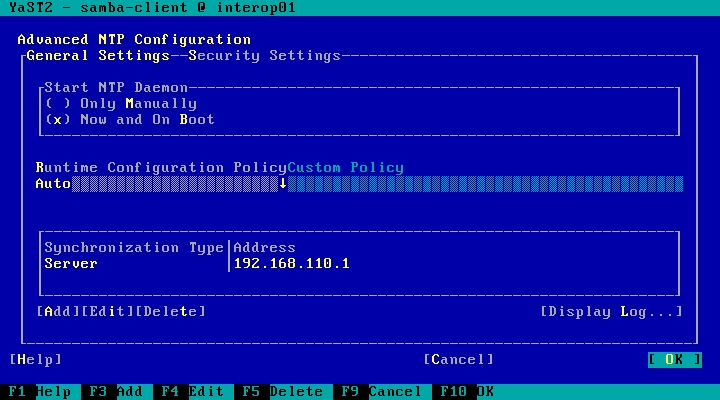
| 5. |
NTP configuration |
||
| 6. |
Initiate the domain join process |
||
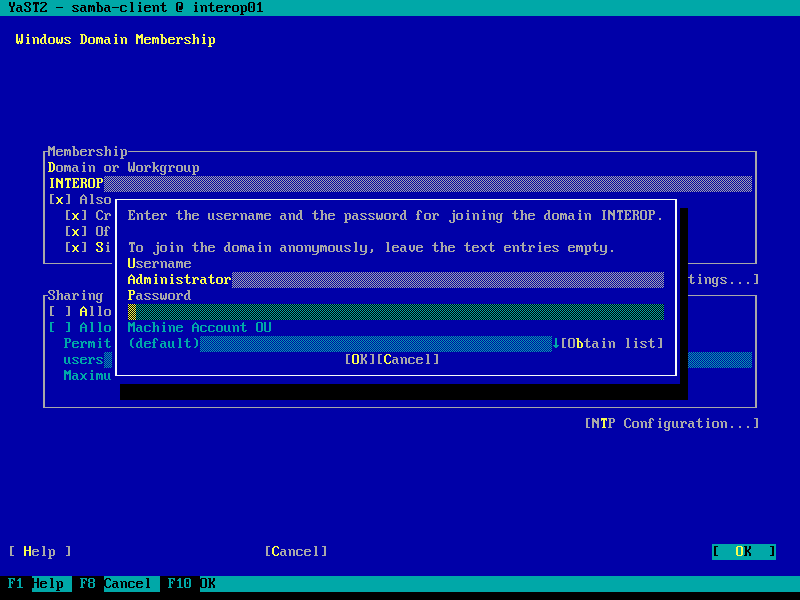
| 7. |
Enter the Administrator password to join |
Generic testing of the AD domain membership
What domain are we joined with?::
# wbinfo --own-domain INTEROP
Get the domain controller for domain INTEROP::
# wbinfo --getdcname=interop WIN200864
Test the availability of the domain controller::
# wbinfo --ping-dc checking the NETLOGON dc connection succeeded
Get information about the domain::
# wbinfo -D interop Name : INTEROP Alt_Name : ad.demo.lan SID : S-1-5-21-3024407125-199061201-3884299293 Active Directory : Yes Native : Yes Primary : Yes
List AD users::
# wbinfo -u INTEROP\administrator INTEROP\guest INTEROP\krbtgt INTEROP\demo INTEROP\sles-apache INTEROP\mssqldbengine
List AD groups::
# wbinfo -g INTEROP\domain computers INTEROP\domain controllers INTEROP\schema admins INTEROP\enterprise admins INTEROP\cert publishers INTEROP\domain admins INTEROP\domain users INTEROP\domain guests INTEROP\group policy creator owners INTEROP\ras and ias servers INTEROP\allowed rodc password replication group INTEROP\denied rodc password replication group INTEROP\read-only domain controllers INTEROP\enterprise read-only domain controllers INTEROP\dnsadmins INTEROP\dnsupdateproxy INTEROP\domain remote desktop users INTEROP\sles web users INTEROP\sqlservermssqlserveradhelperuser$win200864 INTEROP\sqlserver2005sqlbrowseruser$win200864
Successfull login attempt::
# wbinfo --pam-logon=Administrator%MYSECRET plaintext password authentication succeeded
Login attempt with an unknown user::
# wbinfo --pam-logon=Admin%MYSECRET plaintext password authentication failed error code was NT_STATUS_NO_SUCH_USER (0xc0000064) error message was: No such user pam_logon failed for gnyers%asdfsadf
Login attempt with an incorrect password::
# wbinfo --pam-logon=Administrator%IncorrectPassword plaintext password authentication failed error code was NT_STATUS_WRONG_PASSWORD (0xc000006a) error message was: Wrong Password pam_logon failed for Administrator%asdfsadf
Use Active Directory for authentication
PAM and login
Without any changes, Active Directory can be used as authentication source. If the user directory is not available, pam_winbind will also create it.
# tail -f /var/log/messages | grep login Mar 10 21:05:13 interop01 login[3039]: pam_winbind(login:auth): getting password (0x00000390) Mar 10 21:05:13 interop01 login[3039]: pam_winbind(login:auth): pam_get_item returned a password Mar 10 21:05:13 interop01 login[3039]: pam_winbind(login:auth): user 'INTEROP\Administrator' granted access Mar 10 21:05:13 interop01 login[3039]: pam_winbind(login:account): user 'INTEROP\administrator' granted access
Counter proof, trying to log in with incorrect password:
Mar 10 21:12:31 interop01 login[2651]: pam_winbind(login:auth): getting password (0x00000390) Mar 10 21:12:31 interop01 login[2651]: pam_winbind(login:auth): pam_get_item returned a password Mar 10 21:12:31 interop01 login[2651]: pam_winbind(login:auth): request wbcLogonUser failed: WBC_ERR_AUTH_ERROR, PAM error: PAM_AUTH_ERR (7), NTSTATUS: NT_STATUS_LOGON_FAILURE, Error message was: Logon failure Mar 10 21:12:31 interop01 login[2651]: pam_winbind(login:auth): user 'INTEROP\Administrator' denied access (incorrect password or invalid membership) Mar 10 21:12:31 interop01 login[2651]: FAILED LOGIN 2 FROM /dev/tty1 FOR INTEROP\administrator, Authentication failure
SASL and Kerberos enabled applications
Simple Authentication and Security Layer (SASL) is a framework for authentication and data security in Internet protocols. It decouples authentication mechanisms from application protocols, in theory allowing any authentication mechanism supported by SASL to be used in any application protocol that uses SASL.
Even Unix users may "impersonate" AD users:
# id
uid=0(root) gid=0(root) groups=0(root)
# klist
klist: No credentials cache found (ticket cache FILE:/tmp/krb5cc_0)
# kinit Administrator
Password for Administrator@AD.DEMO.LAN:
# klist
Ticket cache: FILE:/tmp/krb5cc_0
Default principal: Administrator@AD.DEMO.LAN
Valid starting Expires Service principal
03/10/13 23:54:15 03/11/13 09:54:23 krbtgt/AD.DEMO.LAN@AD.DEMO.LAN
renew until 03/11/13 23:54:15
using ldapsearch with SASL authentication:
# ldapsearch -h win200864.ad.demo.lan -b 'cn=Users,dc=ad,dc=demo,dc=lan' -LLL '(givenname=interop)' cn SASL/GSSAPI authentication started SASL username: Administrator@AD.DEMO.LAN SASL SSF: 56 SASL data security layer installed. dn: CN=Interop Demo,CN=Users,DC=ad,DC=demo,DC=lan cn: Interop Demo
Note: the Kerberos cache now stores a ticket for the LDAP service
# klist
Ticket cache: FILE:/tmp/krb5cc_0
Default principal: Administrator@AD.DEMO.LAN
Valid starting Expires Service principal
03/10/13 23:54:15 03/11/13 09:54:23 krbtgt/AD.DEMO.LAN@AD.DEMO.LAN
renew until 03/11/13 23:54:15
03/10/13 23:54:34 03/11/13 09:54:23 ldap/win200864@
renew until 03/11/13 23:54:15
03/10/13 23:54:34 03/11/13 09:54:23 ldap/win200864@AD.DEMO.LAN
renew until 03/11/13 23:54:15
#
The Samba tool smbclient supports Kerberos authetication:
# smbclient -k //win200864/Share
OS=[Windows Server 2008 R2 Standard 7601 Service Pack 1] Server=[Windows Server 2008 R2 Standard 6.1]
smb: \> dir
. D 0 Thu Jan 10 16:41:52 2013
.. D 0 Thu Jan 10 16:41:52 2013
New Text Document.txt A 813 Thu Jan 10 16:41:52 2013
This document is created on the dc.txt.txt A 50 Fri Oct 19 23:01:55 2012
40857 blocks of size 1048576. 28362 blocks available
smb: \> exit
And again, the Kerberos ticket cache is growing:
# klist
Ticket cache: FILE:/tmp/krb5cc_0
Default principal: Administrator@AD.DEMO.LAN
Valid starting Expires Service principal
03/10/13 23:54:15 03/11/13 09:54:23 krbtgt/AD.DEMO.LAN@AD.DEMO.LAN
renew until 03/11/13 23:54:15
03/10/13 23:54:34 03/11/13 09:54:23 ldap/win200864@
renew until 03/11/13 23:54:15
03/10/13 23:54:34 03/11/13 09:54:23 ldap/win200864@AD.DEMO.LAN
renew until 03/11/13 23:54:15
03/10/13 23:59:31 03/11/13 09:54:23 cifs/win200864@AD.DEMO.LAN
renew until 03/11/13 23:54:15
#
Other Samba tools supporting Kerberos authentication:
- smbcacls
- smbcquotas
Use Active Directory for authorization
Create group in Active Directory
Execute this on the AD domain controller to create "SLES Shell Users", which will be used to restrict interactive access on SLES systems:
C:\Users\Administrator > dsadd group "cn=SLES Shell Users,cn=Users,dc=ad,dc=demo,dc=lan" -secgrp yes -scope g -desc "Users with shell access on SLES systems" -members "cn=Administrator,cn=Users,dc=ad,dc=demo,dc=lan"
Restrict shell access to a specific group
The YaST *Windows Domain Membership* module is not yet capable of configuring restrictions to shell access based on an Active Directory group. To achieve this, the ``require_membership_of`` parameter must be manually set in ``/etc/security/pam_winbind.conf``.
Allow only members of the group "SLES Shell Users"::
# egrep -v "^[;#]|^$" /etc/security/pam_winbind.conf [global] cached_login = yes krb5_auth = yes krb5_ccache_type = FILE debug = yes cached_login = yes require_membership_of = "SLES Shell Users"
Testing pam_winbind authentication
Without restrictions on shell access
Oct 28 21:08:18 interop02 login[7814]: pam_winbind(login:auth): getting password (0x00000390) Oct 28 21:08:18 interop02 login[7814]: pam_winbind(login:auth): pam_get_item returned a password Oct 28 21:08:18 interop02 login[7814]: pam_winbind(login:auth): user 'interop\demo' granted access Oct 28 21:08:18 interop02 login[7814]: pam_winbind(login:account): user 'demo' granted access
After activating restrictions to allow shell access only to the members of AD group "SLES Shell Users"
Oct 28 21:11:48 interop02 login[7887]: pam_winbind(login:auth): [pamh: 0x60b020] ENTER: pam_sm_authenticate (flags: 0x0000) Oct 28 21:11:48 interop02 login[7887]: pam_winbind(login:auth): getting password (0x000003d1) Oct 28 21:11:48 interop02 login[7887]: pam_winbind(login:auth): pam_get_item returned a password Oct 28 21:11:48 interop02 login[7887]: pam_winbind(login:auth): Verify user 'interop\demo' Oct 28 21:11:48 interop02 login[7887]: pam_winbind(login:auth): CONFIG file: require_membership_of 'SLES Shell Users' Oct 28 21:11:48 interop02 login[7887]: pam_winbind(login:auth): CONFIG file: krb5_ccache_type 'FILE' Oct 28 21:11:48 interop02 login[7887]: pam_winbind(login:auth): enabling krb5 login flag Oct 28 21:11:48 interop02 login[7887]: pam_winbind(login:auth): enabling cached login flag Oct 28 21:11:48 interop02 login[7887]: pam_winbind(login:auth): enabling request for a FILE krb5 ccache Oct 28 21:11:48 interop02 login[7887]: pam_winbind(login:auth): no sid given, looking up: SLES Shell Users Oct 28 21:11:48 interop02 login[7887]: pam_winbind(login:auth): request wbcLogonUser failed: WBC_ERR_AUTH_ERROR, PAM error: PAM_AUTH_ERR (7), NTSTATUS: NT_STATUS_LOGON_FAILURE, Error message was: Logon failure Oct 28 21:11:48 interop02 login[7887]: pam_winbind(login:auth): user 'interop\demo' denied access (incorrect password or invalid membership) Oct 28 21:11:48 interop02 login[7887]: pam_winbind(login:auth): [pamh: 0x60b020] LEAVE: pam_sm_authenticate returning 7 (PAM_AUTH_ERR)
Confirmation of restricted access: login with a user that is member of the AD group "SLES Shell Users"
Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:auth): [pamh: 0x60b020] ENTER: pam_sm_authenticate (flags: 0x0000) Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:auth): getting password (0x000003d1) Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:auth): pam_get_item returned a password Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:auth): Verify user 'interop\administrator' Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:auth): CONFIG file: require_membership_of 'SLES Shell Users' Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:auth): CONFIG file: krb5_ccache_type 'FILE' Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:auth): enabling krb5 login flag Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:auth): enabling cached login flag Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:auth): enabling request for a FILE krb5 ccache Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:auth): no sid given, looking up: SLES Shell Users Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:auth): request wbcLogonUser succeeded Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:auth): user 'interop\administrator' granted access Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:auth): request returned KRB5CCNAME: FILE:/tmp/krb5cc_10001 Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:auth): Returned user was 'administrator' Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:auth): [pamh: 0x60b020] LEAVE: pam_sm_authenticate returning 0 (PAM_SUCCESS) Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:account): [pamh: 0x60b020] ENTER: pam_sm_acct_mgmt (flags: 0x0000) Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:account): user 'administrator' granted access Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:account): [pamh: 0x60b020] LEAVE: pam_sm_acct_mgmt returning 0 (PAM_SUCCESS) Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:setcred): [pamh: 0x60b020] ENTER: pam_sm_setcred (flags: 0x0002) Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:setcred): PAM_ESTABLISH_CRED not implemented Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:setcred): [pamh: 0x60b020] LEAVE: pam_sm_setcred returning 0 (PAM_SUCCESS) Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:session): [pamh: 0x60b020] ENTER: pam_sm_open_session (flags: 0x0000) Oct 28 21:12:55 interop02 login[7905]: pam_winbind(login:session): [pamh: 0x60b020] LEAVE: pam_sm_open_session returning 0 (PAM_SUCCESS)
With plain username and password::
# smbclient -U 'Administrator%MYSECRET' //win200864/Share
Using a credentials file::
# smbclient -A /root/.smb.credentials //win200864/Share Domain=[INTEROP] OS=[Windows Server 2008 R2 Standard 7601 Service Pack 1] Server=[Windows Server 2008 R2 Standard 6.1] smb: \>
Manually::
# mount -o username=Administrator,password=MYSECRET //win200864/Share /mnt/win200864-Share Domain=[INTEROP] OS=[Windows Server 2008 R2 Standard 7601 Service Pack 1] Server=[Windows Server 2008 R2 Standard 6.1] smb: \>
From /etc/fstab during boot::
# grep win200864 /etc/fstab //win200864/Share /mnt/win200864-Share cifs credentials=/root/.smb.credentials 0 0
See Credentials file
From /etc/samba/smbfstab::
# //win200864/Share2 /mnt/win200864-Share2 cifs username=tridge,password=foobar
Problem::
# ls -l /mnt/win200864-Share/ total 5 -rwxr-xr-x 0 root root 813 Jan 10 15:41 New Text Document.txt -rwxr-xr-x 0 root root 50 Oct 19 21:01 This document is created on the dc.txt.txt #
Please note that the users
Credentials file
The content of the credentials file::
# cat /root/.smb.credentials username=INTEROP\Administrator password=MYSECRET
Make sure that the credentials file is only readable by root::
# ls -l /root/.smb.credentials -rw------- 1 root root 49 Mar 7 13:27 /root/.smb.credentials
See also:
- mount.cifs(8)
- cifs.idmap(8)
- request-key.conf(5)
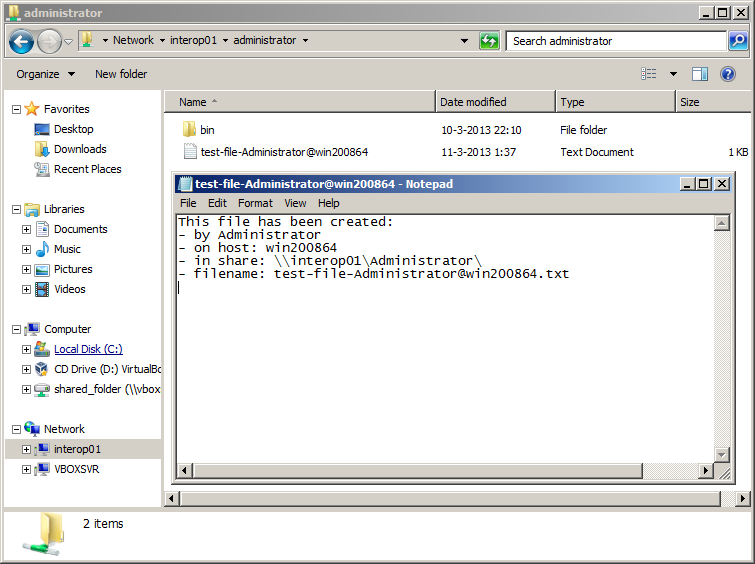
Please note: access to the Samba shares is transparent, that is: authentication of Administrator is conducted by Samba and AD, without the user needing to (re-)enter a password.
References
- Samba in the SUSE Linux Enterprise Server Administration Guide
- Microsoft TechNet: Authenticate Linux Clients with Active Directory
- Jurjen Bokma's collection of Linux and AD HOWTOs http://jurjenbokma.com/ApprenticesNotes/Linux-AD-auth.html
[TODO]: Mention other references