User:Gnyers/InteropDemo/ApacheAuthAndAuthzIntegrationWithADDomain
Tested on openSUSE
Recommended articles
Integrating with Active Directory as authentication and authorization source is a frequent use case in mixed Linux and Windows environments. Winbind, a component of Samba, provides not only the necessary integration with AD but also a PAM module to authenticate and authorize Linux users
This HOWTO uses Samba 3.6
Please note: This article is not yet finished
Introduction
In order for users not to have to (re-)enter AD credentials when they access a web page or application served by the Apache web server an integration of Apache with Active Directory is needed.
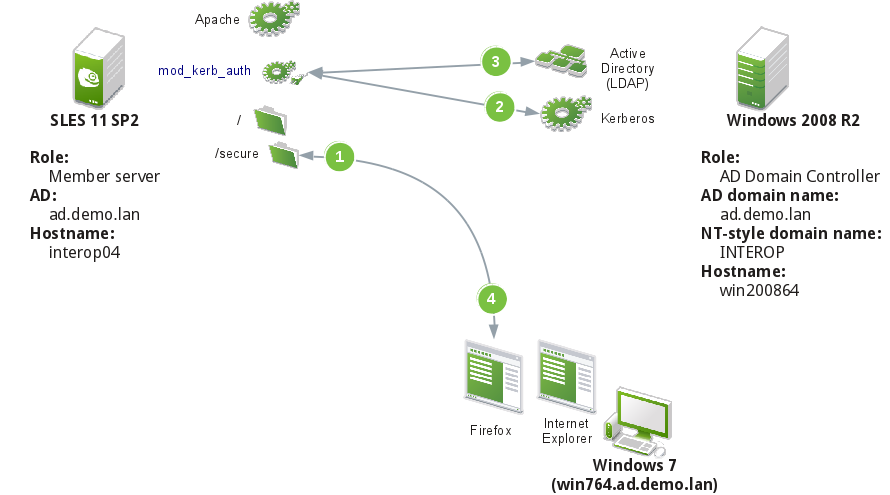
Server:
- Apache2, mod_auth_kerb
Clients:
- Windows 7, Windows XP
- Browsers:
- Firefox; Add-ons: Live HTTP Headers
- Internet Explorer
- Chrome
Integration of Apache with Active Directory
Preparations in Active Directory
Create a group, which will be used to restrict access to the secure website:
C:\Users\Administrator > dsadd group "cn=SLES Web Users,cn=Users,dc=ad,dc=demo,dc=lan" -secgrp yes -scope g -desc "Apache on SLES is restricted to these users" -members "cn=Administrator,cn=Users,dc=ad,dc=demo,dc=lan"
Create a service account for Apache, which will be used to grant access based on a group membership in Active Directory::
C:\Users\Administrator>dsadd user "cn=sles-apache,cn=Users,dc=ad,dc=demo,dc=lan" -samid sles-apache -upn sles-apache -pwd Suse123. -acctexpires never -mustchpwd no -pwdneverexpires yes -memberOf "cn=SLES Web Users,cn=Users,dc=ad,dc=demo,dc=lan" -display "Apache Service Account" -desc "Apache service account to connect to Active Direcory. Purpose of this account is for Apache to retrieve group membership in order to restrict access to pages or sites"
Preparations on SLES and Apache
Kerberos
Configure Kerberos::
# cat /etc/krb5.conf
[libdefaults]
default_realm = AD.DEMO.LAN
clockskew = 300
[realms]
AD.DEMO.LAN = {
kdc = 192.168.110.32
default_domain = ad.demo.lan
admin_server = 192.168.110.32
}
[logging]
kdc = FILE:/var/log/krb5/krb5kdc.log
admin_server = FILE:/var/log/krb5/kadmind.log
default = SYSLOG:NOTICE:DAEMON
[domain_realm]
.ad.demo.lan = AD.DEMO.LAN
Create the keytab::
# net ads keytab add HTTP -U sles-apache%MYSECRET
Or on Windows::
#
List the security principals: ::
# klist -e -k /etc/apache2/conf.d/sles-apache.krb5.keytab Keytab name: FILE:/etc/krb5.keytab KVNO Principal ---- -------------------------------------------------------------------------- 4 HTTP/interop04.ad.demo.lan@AD.DEMO.LAN (DES cbc mode with CRC-32) 4 HTTP/interop04.ad.demo.lan@AD.DEMO.LAN (DES cbc mode with RSA-MD5) 4 HTTP/interop04.ad.demo.lan@AD.DEMO.LAN (ArcFour with HMAC/md5) 4 HTTP/interop04@AD.DEMO.LAN (DES cbc mode with CRC-32) 4 HTTP/interop04@AD.DEMO.LAN (DES cbc mode with RSA-MD5) 4 HTTP/interop04@AD.DEMO.LAN (ArcFour with HMAC/md5)
Set ownership of keytab file and restrict access to it::
# chown wwwrun:www /etc/apache2/conf.d/sles-apache.krb5.keytab # chmod 0600 /etc/apache2/conf.d/sles-apache.krb5.keytab
Apache mod_auth_kerb
Install the mod_auth_kerb module::
# zypper in apache2-mod_auth_kerb
Configure the module::
# cat /etc/apache/conf.d/apache-integration-with-ad.conf LoadModule auth_kerb_module /usr/lib64/apache2/mod_auth_kerb.so LoadModule ldap_module /usr/lib64/apache2/mod_ldap.so LoadModule authnz_ldap_module /usr/lib64/apache2/mod_authnz_ldap.so <Location /secure> # Configuration for auth_kerb AuthName "---Restricted Access, please use your Active Directory credentials---" AuthType Kerberos KrbMethodNegotiate on KrbMethodK5Passwd on Krb5Keytab /etc/apache2/conf.d/sles-apache.krb5.keytab KrbAuthRealms AD.DEMO.LAN KrbServiceName HTTP/interop04.ad.demo.lan@AD.DEMO.LAN KrbLocalUserMapping On # Configuration for authnz_ldap AuthLDAPBindDN cn=sles-apache,cn=Users,dc=ad,dc=demo,dc=lan AuthLDAPBindPassword SecretPassword AuthLDAPURL "ldap://win200864.ad.demo.lan:389/dc=ad,dc=demo,dc=lan?sAMAccountName" AuthLDAPGroupAttribute member Require ldap-group cn=SLES Web Users,cn=Users,dc=ad,dc=demo,dc=lan </Location>
References
- Single Sign On with ZCP: (how to create keytab files on Windows for Apache etc..): http://doc.zarafa.com/6.40/Administrator_Manual/en-US/html/_single_sign_on_with_zcp.html
- Apache ``mod_authnz_ldap`` documentation: http://httpd.apache.org/docs/2.2/mod/mod_authnz_ldap.html
- Apache ``mod_ldap`` documentation: http://httpd.apache.org/docs/2.2/mod/mod_ldap.html
Preparations on the user profiles
Browser configuration: Firefox
Useful Firefox Add-ons:
- Live HTTP Headers: This Add-on may be used for troubleshooting the authentication process by tracing the headers exchanged between the browser and the web server
Home page: http://livehttpheaders.mozdev.org/
- Integrated Authentication for Firefox: This Add-on makes the management of the list of sites, for which Firefox will enable the TLM and SPNEGO authentication protocol.
Home page: https://code.google.com/p/firefox-ntlmauth/
Enable Kerberos Negotiation without the "Integrated Authentication for Firefox" Add-on:
- type in the URL bar: about:config
- filter on "negotiate"
- change the follwing settings:
- network.negotiate-auth.delegation-uris = *site-list*
Examples for *site-list*: ".ad.demo.lan, https://intranet.example.com"
See also:
- Mozilla Developer Network, Integrated Authentication: https://developer.mozilla.org/en-US/docs/Integrated_Authentication
- Firefox config parameter "network.automatic-ntlm-auth.trusted-uris"
- RFC2478: The Simple and Protected GSS-API Negotiation Mechanism: http://tools.ietf.org/html/rfc2478
- RFC4178: The Simple and Protected Generic Security Service Application Program Interface (GSS-API) Negotiation Mechanism: http://tools.ietf.org/html/rfc4178
Browser configuration: Internet Explorer
Integrated Windows Authentication
See also:
- Microsoft TechNet: http://technet.microsoft.com/en-us/library/cc779070%28v=ws.10%29.aspx
1.) Unconfigured Kerberos authentication
File:Interop-integrate-apache-with-ad-configure-ie-for-integrated-auth-01.png
2.) Let's ``add ad.demo.lan`` subdomain to the *Local Internet* security zone.
- Select **Tools** > **Internet Options**
- Select Tab **Security**
- Click on **Sites**
File:Interop-integrate-apache-with-ad-configure-ie-for-integrated-auth-02.png
3.) Click on **Advanced** File:Interop-integrate-apache-with-ad-configure-ie-for-integrated-auth-03.png
4.)
- Type ``http://*.ad.demo.lan``
- Click **Add**
File:Interop-integrate-apache-with-ad-configure-ie-for-integrated-auth-04.png
5.) close the dialog [[File:Interop-integrate-apache-with-ad-configure-ie-for-integrated-auth-05.png
6.) After reloading the page, the browser transparently performs the authentication, without user interaction
File:Interop-integrate-apache-with-ad-configure-ie-for-integrated-auth-06.png
Apache log examples
Response to an unauthenticated browser request in ``access_log``::
192.168.110.210 - - [27/Oct/2012:12:54:21 +0200] "GET / HTTP/1.1" 401 - "-" "Mozilla/5.0 (Windows NT 5.1; rv:16.0) Gecko/20100101 Firefox/16.0"
Response to an correctly negotiated browser request in ``access_log``::
192.168.110.210 - demo@AD.DEMO.LAN [27/Oct/2012:12:54:21 +0200] "GET / HTTP/1.1" 200 44 "-" "Mozilla/5.0 (Windows NT 5.1; rv:16.0) Gecko/20100101 Firefox/16.0"
Response to a request, for which no Kerberos authentication could be performed, due to time differences. The difference was caused by incorrect timezone settings ::
[Sun Oct 28 14:33:12 2012] [error] [client 192.168.110.32] gss_accept_sec_context() failed: Unspecified GSS failure. Minor code may provide more information (, Ticket not yet valid)
References
- Home page of the mod-auth-kerb Apache module: http://modauthkerb.sourceforge.net/
- Microsoft TechNet: Authenticate Linux Clients with Active Directory http://technet.microsoft.com/en-au/magazine/2008.12.linux.aspx
[TODO]: Mention other references
