openSUSE:UEFI Secure boot using qemu-kvm
If you want to contribute, please read the rules for this wiki and if you have any questions, don't hesitate to contact the wiki team, we are more then willing to help you! :-)
This is based on James Bottomley <James.Bottomley@parallels.com>'s approach:
Prepare Environment
Prepare a openSUSE 12.2 machine
Yes! Just use a openSUSE 12.2 DVD to install a machine. Please remember need use 64-bits openSUSE because Jeremy's efi signing tools only really do x86_64 binaries.
Install OVMF
Add James's repo on OBS:
zypper ar -f -n UEFI http://download.opensuse.org/repositories/home:/jejb1:/UEFI/openSUSE_12.2/home:jejb1:UEFI.repo
OVMF is a UEFI BIOS image build from EDK2 used by qemu-kvm, let's install:
# zypper in OVMF
Build James's efitools
James's git have a efitools set for test UEFI secure boot. Clone it:
# cd ~/ # git clone git://git.kernel.org/pub/scm/linux/kernel/git/jejb/efitools.git
Before compiling it, please install the standard dev environment gnu-efi, help2man and sbsigntools as well as libopenssl-devel libraries used by efitools and finally of course you also need gcc and make:
# zypper in gnu-efi help2man sbsigntools gcc make libopenssl-devel
Then, yes, make it:
# cd ~/efitools # make
Please make sure generated out the following .efi files:
# ls *.efi HelloWorld.efi HelloWorld-signed.efi LockDown.efi LockDown-signed.efi
Prepare hda for Qemu
We will need to import PK/KEK/DB to UEFI BIOS for secure boot testing, and, also need to run some *.efi executable to verify security. So, we should prepare a hda contents folder then feed it to qemu-kvm later:
# cd ~/ # mkdir hda-contents
Copy PK.crt, KEK.crt and *.efi file from efitools folder to ~/hda-contents:
# cd ~/hda-contents # cp ~/efitools/KEK.crt ~/efitools/DB.crt ~/efitools/PK.crt ~/efitools/*.efi ./ # ls ~/hda-contents
DB.crt HelloWorld.efi HelloWorld-signed.efi KEK.crt LockDown.efi LockDown-signed.efi PK.crt
Due to openSUSE certificate is PEM format, we need transfer to DER format for enroll to UEFI BIOS:
# openssl x509 -in KEK.crt -outform DER -out KEK.der # openssl x509 -in PK.crt -outform DER -out PK.der # openssl x509 -in DB.crt -outform DER -out DB.der
Launch qemu-kvm with UEFI
The BIOS image folder of OVMF rpm is in /usr/share/qemu-ovmf/bios :
linux-8wu0:~/efitools # rpm -ql OVMF /usr/share/qemu-ovmf /usr/share/qemu-ovmf/README /usr/share/qemu-ovmf/bios /usr/share/qemu-ovmf/bios/bios.bin /usr/share/qemu-ovmf/bios/vgabios-cirrus.bin /usr/share/qemu-ovmf/efi /usr/share/qemu-ovmf/efi/HelloWorld.efi
Run qemu-system-x86_64 to launch virtual machine:
# qemu-system-x86_64 -L /usr/share/qemu-ovmf/bios -hda fat:hda-contents/
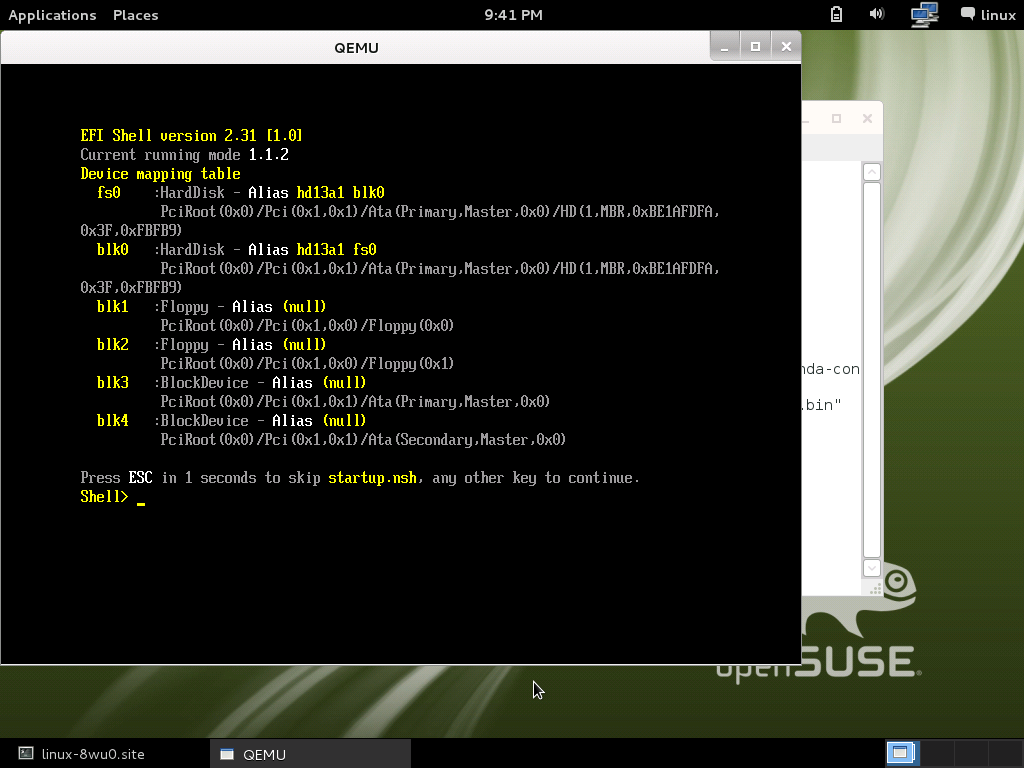
After boot progress finished, will see UEFI shell prompt show up like following:
Test Secure Boot
Enable Secure Boot
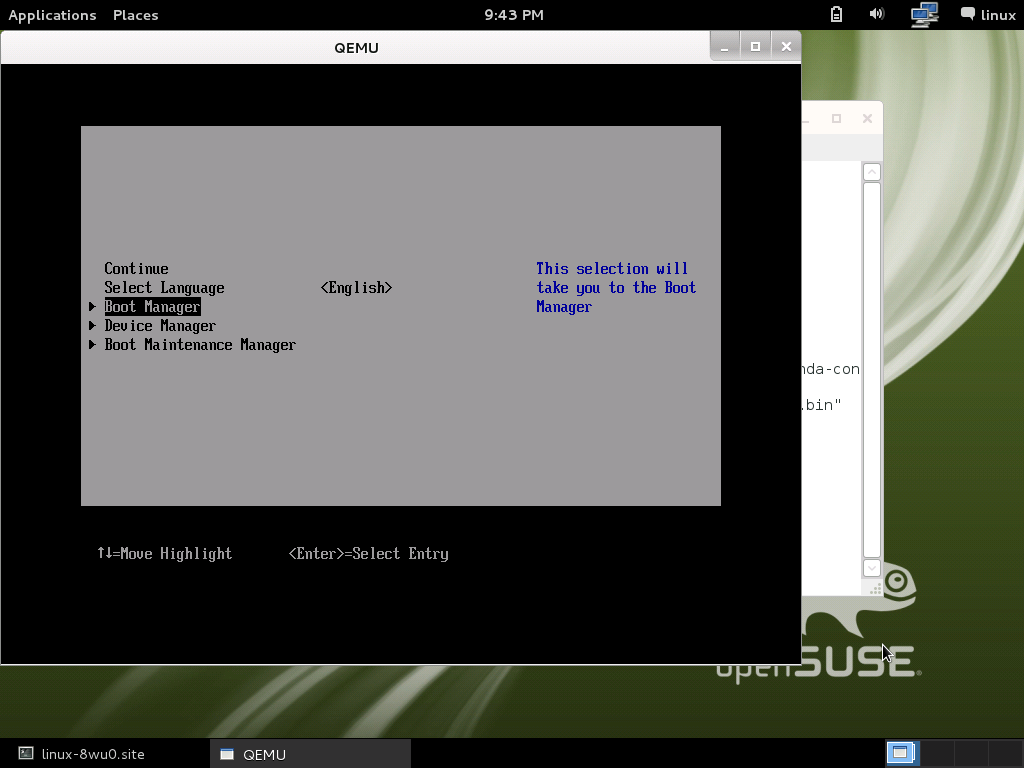
Close UEFI shell then go to UEFI configuration menu:
Shell> exit
Go to Secure Boot Mode option:
Device Manager >> Secure Boot Configuration >> Secure Boot Mode
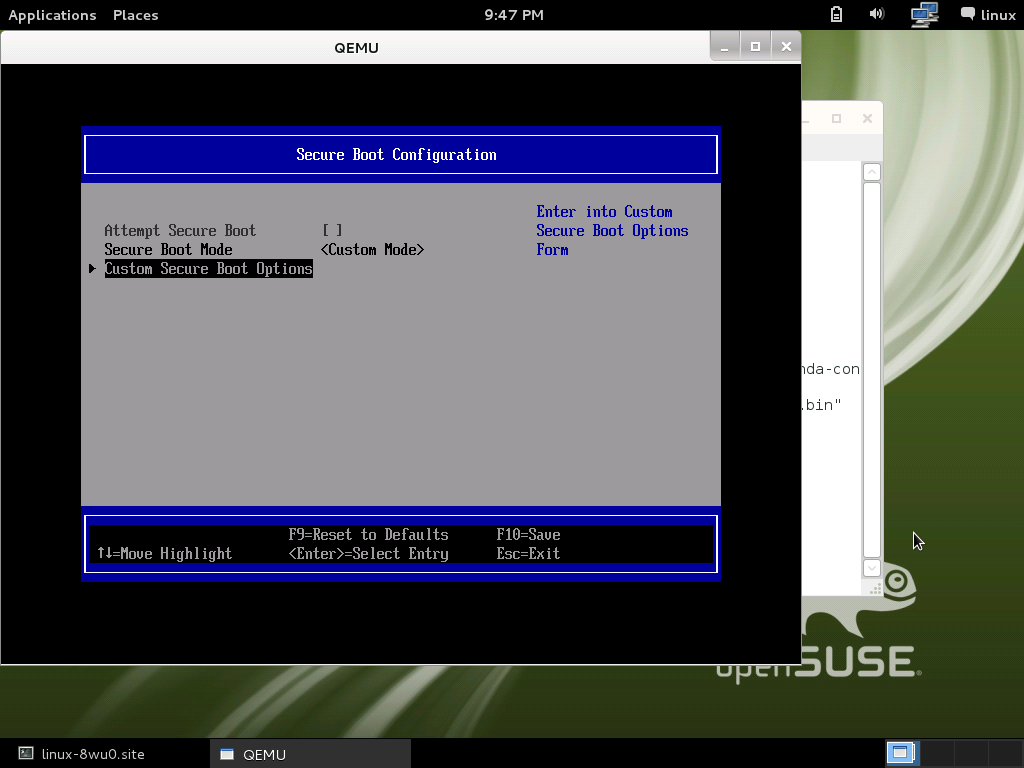
Change it to "Custom Mode":
After change to "Custom Mode", will show up Custom Secure Boot Options
Import PK/KEK
Import PK
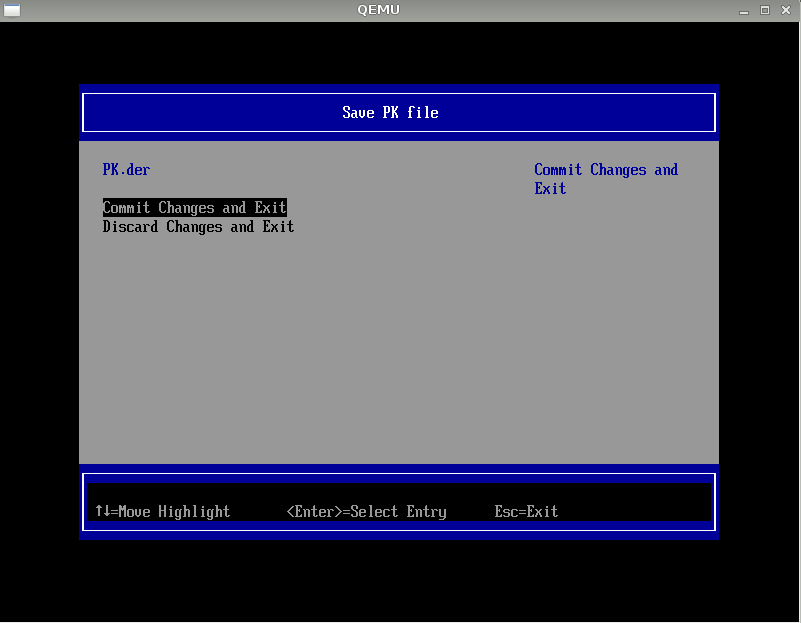
Please go to the following option:
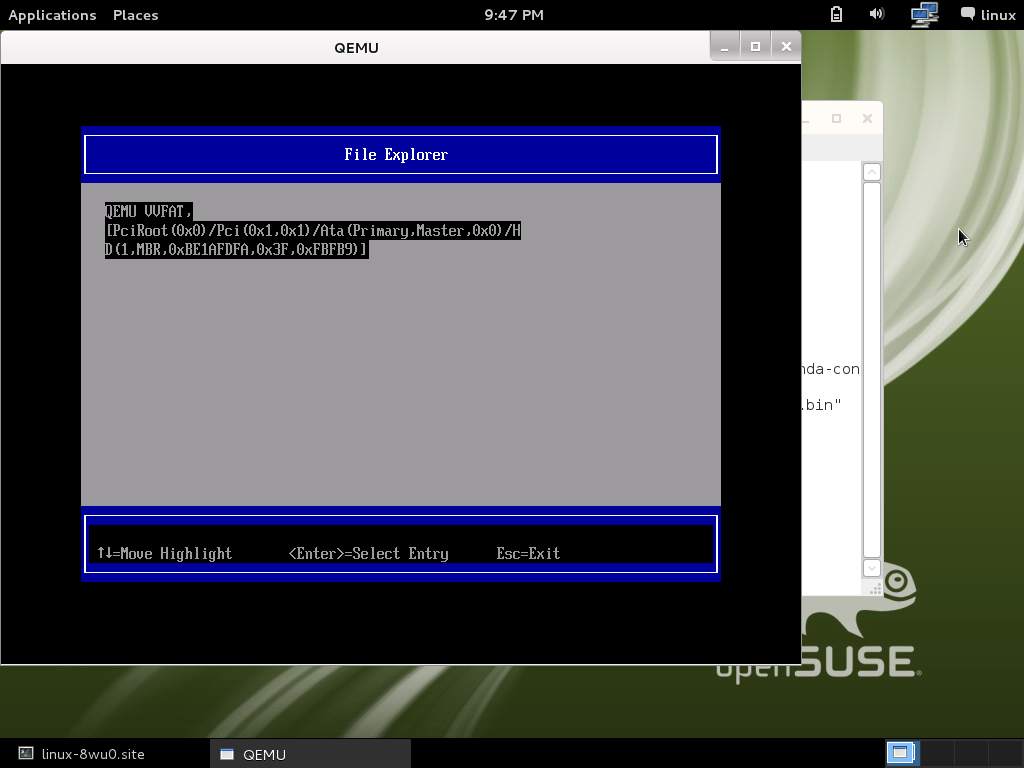
Custom Secure Boot Options >> PK Options >> Enroll PK >> Enroll PK Using File
Select the one and only one HD space:
Select PK.der
Select "Commit Changes and Exit", then PK will import to DB in UEFI BIOS.
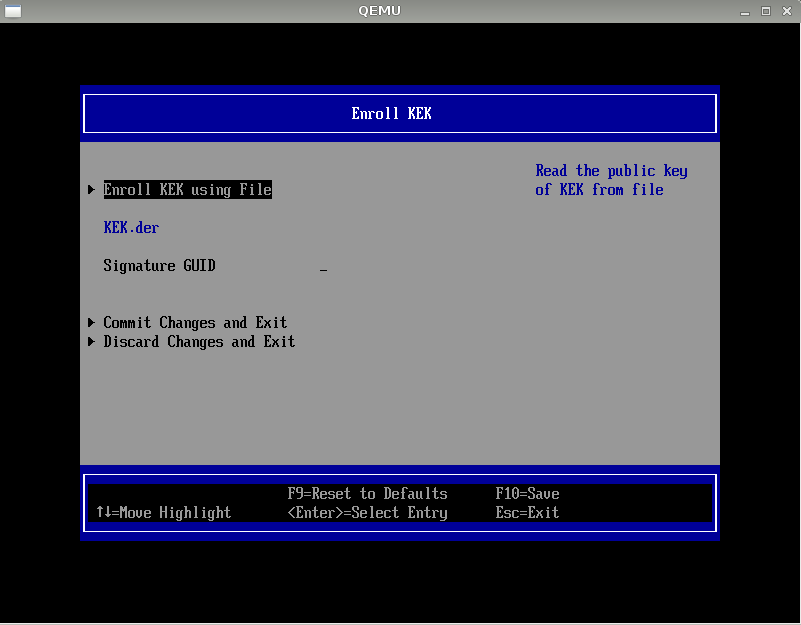
Import KEK
The process the same with PK, just need use "KEK Options":
Custom Secure Boot Options >> KEK Options >> Enroll KEK >> Enroll KEK Using File
Then select "KEK.der" file, don't forget "Commit Changes and Exit"!
Executing LockDown.efi
In case if you cannot locate the PK.cer file, then quit QEMU and restart again ( redo launch qemu-kvm with UEFI )
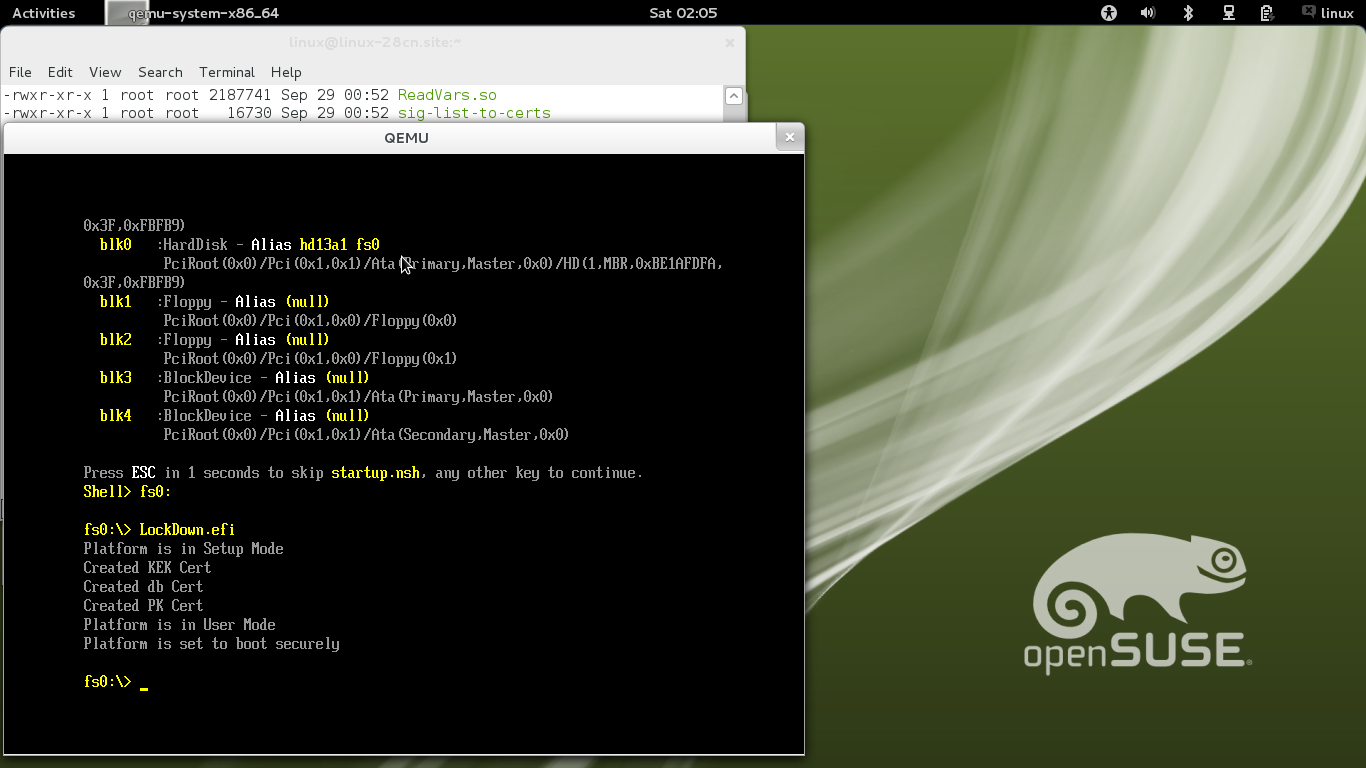
Select "Continue", type "fs0:" and then type "LockDown.efi".
When you type make at folder "efitools", it will generate a set of keys and place them into a binary called LockDown.efi. Execution of this efi binary will provision all the keys and place the platform into Secure Boot enabled User Mode (from this point on, it will only execute signed efi binaries)
Run .efi file
OK! Now We imported PK and KEK, that means we enabled secure boot. Then, we can run HelloWorld efi to verify it.
Press ESC back to the UEFI main menu, select:
Boot Manager >> EFI Internal Shell
you will see the EFI shell prompt show up again.
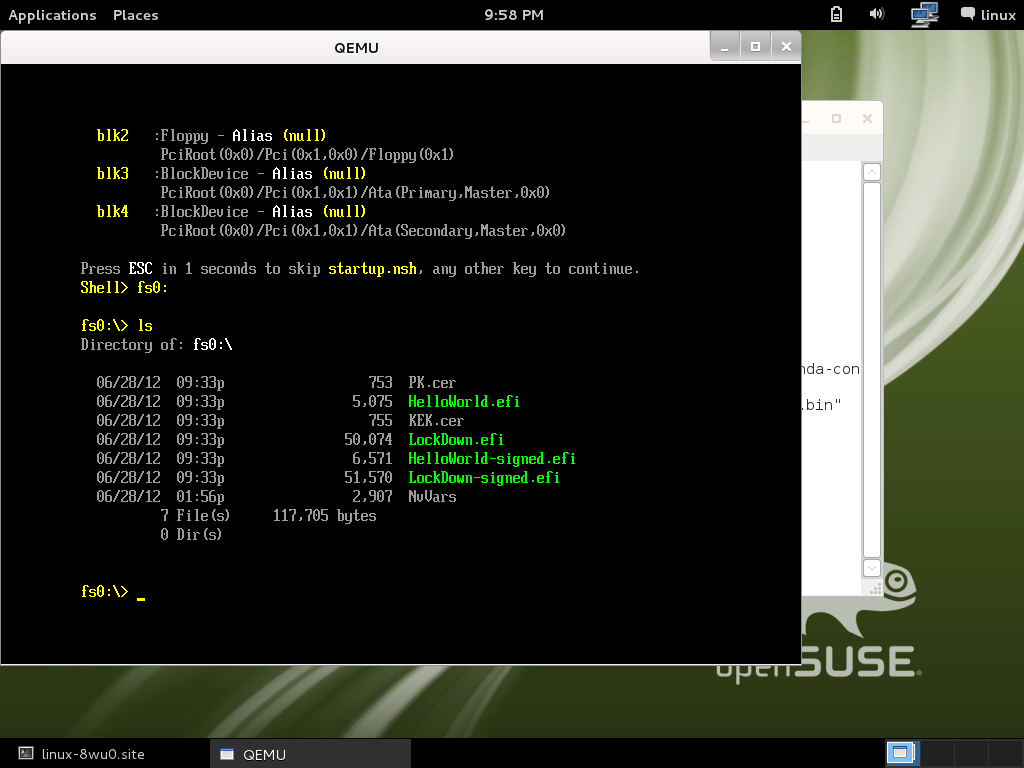
Then we need go to hda-contents because our *.efi executable put there. Key-in fs0 then press enter like DOS:
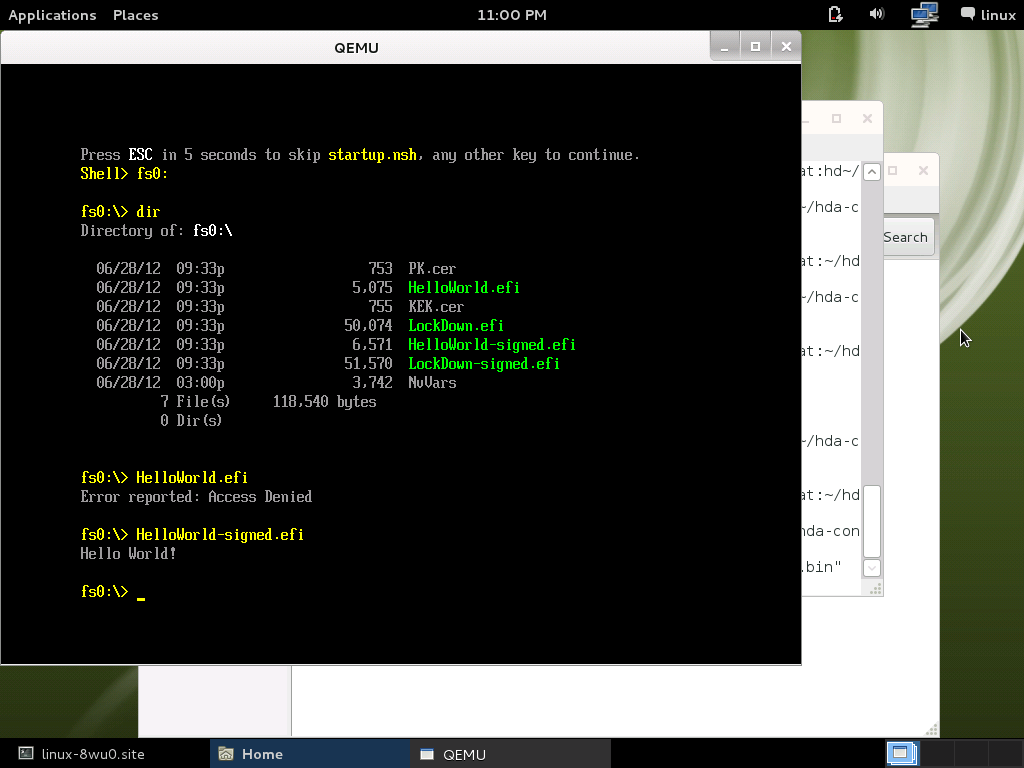
Shell> fs0: fs0:\>
You can use ls or dir to list all files in fs0:
There have 2 HelloWorld* efi file, one is unsigned another is signed.
Run HelloWorld.efi:
fs0:\> HelloWorld.efi Error reported: Access Denied
Yes, it will show up "Access Denied"
Run HelloWorld-signed.efi
fs0:\> HelloWorld-signed.efi Hello World!
OK, pass!
Disable Secure Boot
Then you can try the option for temporary disable secure boot:
Device Manager >> Secure Boot Configuration >> Attempt Secure Boot [x]
Press Enter key to remove the [x] on "Attempt Secure Boot" Back to shell prompt to run HelloWorld.efi, you will find it available, now.
Per information from Insyde, the code path of this option is fully the same with "enabled secure boot", just it ignore the result of secure boot check.
running openSUSE
In order to get openSUSE running the DB.crt and KEK.crt keys will have to be replaced by the public Microsoft keys:
# cd ~/hda-contents # wget http://www.microsoft.com/pkiops/certs/MicCorUEFCA2011_2011-06-27.crt # wget http://www.microsoft.com/pkiops/certs/MicCorKEKCA2011_2011-06-24.crt
Now get yourself an openSUSE image of your choice, prepare a virtual harddisk with qemu-img and start again qemu:
# qemu-system-x86_64 -L /usr/share/qemu-ovmf/bios -hda [your virtual harddisk] -cdrom [your iso img] -hdb fat:~/hda-contents/
Now like described before in the section #Import PK/KEK enroll the PK-Key: 'PK.der' (you can use the KEK-key too if you don't want to create your own PK, but it is better to create your own),the KEK-Key: 'MicCorKEKCA2011_2011-06-24.crt' and the DB-Key: 'MicCorUEFCA2011_2011-06-27.crt'. (Note GUID used to identify Microsoft 77fa9abd-0359-4d32-bd60-28f4e78f784b)
# now boot
Note that in the Installation Setting's Booting section you may have to set the option manually to "Enable Secure Boot:true"
openSUSE CA
For openSUSE CA, the public space for grab it is from shim RPM source on OBS: devel:openSUSE:Factory > shim
Due to openSUSE certificate is PEM format, we need transfer to DER format for enroll to UEFI BIOS:
# openssl x509 -inform PEM -in openSUSE-UEFI-CA-Certificate.crt -outform DER -out openSUSE-UEFI-CA-Certificate.der # openssl x509 -inform PEM -in openSUSE-UEFI-SIGN-Certificate.crt -outform DER -out openSUSE-UEFI-SIGN-Certificate.der
- *UEFI-CA*.der is certificate for enroll to KEK database in UEFI BIOS.
- *UEFI-SIGN*.der is certificate for enroll to db database in UEFI BIOS.
Then enroll them by this procedure: enroll PK, KEK and db
If you want test the openSUSE signed shim, please install shim package, it includes the following files:
# rpm -ql shim /usr/lib64/efi /usr/lib64/efi/MokManager.efi /usr/lib64/efi/shim-opensuse.der /usr/lib64/efi/shim-opensuse.efi /usr/lib64/efi/shim.efi
Please copy shim-opensuse.efi and shim.efi(signed by Microsoft) to hda-contents then launch kvm with OVMF:
# qemu-kvm -L /usr/share/qemu-ovmf/bios -hda fat:<absolute_path_to_user_home_directory>/hda-contents/
Switch to fs0: in shell console, then we can test the openSUSE CA works on signed shim.